AI readiness at risk: complexity and governance are holding back secure deployment
Last Update: 16 September 2025

Three-quarters of IT and security leaders say reducing information complexity is critical for AI readiness. Yet most organisations still lack the governance and controls to deploy AI securely. New global research from Ponemon Institute highlights the gap between ambition and execution.
Key findings at a glance
- Priority vs. proof: 57% rank AI adoption as a top priority. 54% feel confident proving ROI. Yet 53% say reducing AI security and legal risk is “very” or “extremely” difficult.
- Leadership vs. alignment: 55% of CEOs/boards see AI as very important, but only 47% say IT and security goals align with AI strategy.
- Complexity everywhere: Top drivers include unstructured data (44%), IoT growth (46%), and emerging cyber threats (52%). Teams juggle ~15 security tools on average.
- Budget and time: 31% cite insufficient funding, 29% limited time to integrate, and 28% misalignment between IT and security.
- Top risks: Privacy (44%), weak encryption (42%), and poor system configuration from AI over-reliance (40%).
- Mitigations rising: Data security programs (46%), prompt-validation tools (39%), governance frameworks (38%), and staff training on AI-driven threats (39%).
- Adoption trends: Among the 50% already deploying AI, 32% use GenAI today and 26% plan rollout in six months. Agentic AI remains early: 19% live, 16% near-term.
Leadership support is high, but alignment is patchy
Executive sponsorship is no longer the hurdle. However, strategy often outruns enablement. Only 47% report tight alignment between AI goals and IT/security plans. Consequently, teams spin up pilots without the processes, data pipelines, and guardrails that production demands. Many organisations are hiring CAIO/CDO roles to close this gap, yet role clarity and accountability still matter more than titles.
Complexity is the hidden tax on AI readiness
Information sprawl drags down timelines and confidence. Unstructured files, IoT streams, and a sprawling security stack create fragmentation. Therefore, even simple AI use cases inherit brittle inputs and inconsistent controls. Simplify the path in, not the model first.
Practical moves:
- Run AI cybersecurity assessments to test access, logging, encryption, retention, and alignment to ISO 42001 and ISO 27001.
- Apply prompt guarding to block injection and data leakage with allow lists, context isolation, output filters, and human in the loop for higher risk actions.
- Add fraud checks to verify identity, income, and assets, detect duplicates and tampered files, and trigger step up verification when required.
- Standardise intake and consent at the front door.
- Categorise and classify files automatically and route exceptions.
- Extract fields into structured records before they touch core systems.
- Validate totals, identifiers, and periods early.
- Redact sensitive data in working copies by default.
- Cross check and reconcile documents and data before posting, surfacing exceptions for review.
- Assess cybersecurity risk for existing and future AI projects with a single register of use cases, data sensitivity, supplier exposure, controls, and owners.
- Structure data at field level, tag sensitivity and purpose, minimise personal information passed downstream, and enforce least privilege.
- Secure storage and access with encryption in transit and at rest, role based access, retention and legal hold, immutable logs, and access pattern monitoring.
Privacy and security concerns dominate
Privacy risk leads the list, followed by weak crypto hygiene and misconfigurations. Accordingly, leaders are investing in data security programs, governance frameworks, and human training. Evidence is essential. If you cannot show who accessed what, when, and under what policy, audits will stall no matter how clever the model is.
Adoption: GenAI first, Agentic AI next
GenAI is spreading through security operations, productivity, threat detection, and software development. Yet copyright risk, skills gaps, and regulatory uncertainty slow scale-up. Meanwhile, Agentic AI and Service AI remains early but promising. It moves from “assist” to “act,” provided you set policy, logging, and human-in-the-loop checkpoints.
The Path Forward
The findings suggest that while organisations are eager to reap the benefits of AI, their governance, risk management, and information complexity challenges remain major stumbling blocks.
To close the readiness gap, leaders must:
- Run Cybersecurity risk assessments for AI projects
- Engage AI ROI focused business with proven use cases
- Appoint dedicated AI oversight (59% of respondents see this as critical).
- Streamline governance and security policies (56%).
- Reduce overlapping technologies and complexity (55%).
Without addressing these foundations, AI investments risk being undermined by fragmentation, weak security, and misaligned leadership priorities.
A simple readiness blueprint (90 days)
Weeks 1–3 — Pick one weekly workflow
Choose a process with a clear owner and measurable value: time saved, error reduction, or cycle time. Map inputs, approvals, cybersecurity risk assessment for AI projects and “definition of done.”
Weeks 4–8 — Engineer the data path
Replace ad-hoc email with a secure portal. Categorise, classify, extract, and cross-check before data hits systems of record. Redact by default for any external sharing.
Weeks 9–12 — Prove and scale
Publish before/after metrics, document the controls, and template the build for two more use cases.
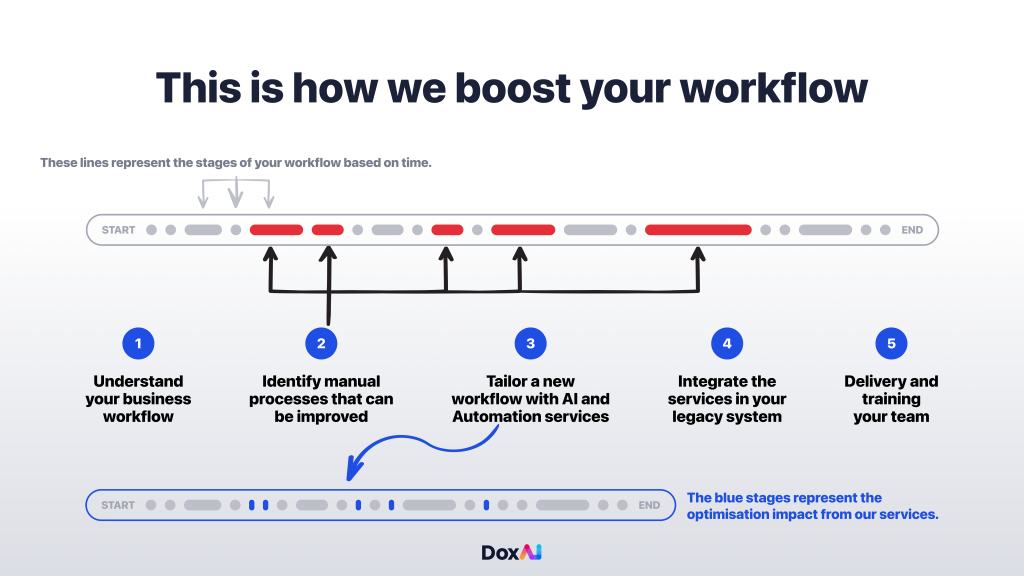
How DoxAI closes the readiness gap
DoxAI reduces complexity and bakes governance into daily work. Each step is modular; together they create an auditable, end-to-end pipeline.
- Cybersecurity Risk Assessment out of the box provides independent risk assessments and continuous monitoring with compliance and resilience reporting, supply chain and vendor risk scoring, and prioritised mitigation in one dashboard.
- Prompt Guarding AI applies policy based controls to AI use by baselining risks, mapping controls to frameworks, monitoring prompts and outputs, and alerting on prompt injection or data leakage.
- Data Exchange automates data & document secure intake or onboarding with checklists, consent capture, reminders, verification of identity and eSignature in one flow. Result: complete packs, fewer chasers.
- Fraud Check AI: First document agnostic fraud activity detection model designed to detect fraudulent activities in any document type, understand the specific document category and subsequently execute automatic fraudulent checking rules designed for the specific document type.
- Categorise AI auto-splits, categorises and tags mixed files into the right document types and structures. Therefore, reviewers start organised.
- Extract AI turns structured and unstructured files into field-level records your systems can use.
- Cross-Check AI fully customisable, capable of cross-checking, validating, calculating, context cross-referencing, image and document structure comparison, and more, across multiple data sets.
- Redact AI offers keyword redaction, regular expression redaction, and automatic detection and redaction of sensitive content, such as PII and BII. It also provides percentage redaction, key context redaction and detection, dynamic query redaction, and redaction of audio and video files.
- AI Agent Marketplace orchestrates the hand-offs with policy controls, audit trails, and rollback, so agents execute steps inside your governance.
- And 70+ AI mircoservices
Bottom line: simplify intake, structure data, verify early, and share safely. Then let agents execute under policy. That is how AI readiness turns into secure deployment and measurable ROI.
Ready to move from pilots to production?
Book a 30-minute use-case session.

About DoxAI
DoxAI is your trusted process automation partner, enabling to transition from outdated systems to cutting-edge AI technology. Our platform streamlines the collection, management, processing, and storage of data, enhancing security, reducing operational costs, and boosting customer engagement. DoxAI empowers providers to automate and secure every step of their data and document handling processes. Our suite of products supports end-to-end workflows, from intake to archiving, ensuring privacy, compliance and faster service delivery.
Security at Scale
In addition, we enforce strict security measures, including encryption at rest and in transit, robust access controls, and multi-factor authentication. As a SOC2 Type 2, HIPPA, GDPR and PCI DSS certified organisation, we undergo regular audits and penetration tests to maintain top-tier data protection. We deliver a scalable cloud-based infrastructure that supports your business growth without compromising performance. Our service-oriented architecture automates expansion, and we store data locally to meet sovereignty and regulatory requirements.
Our solutions are agnostic to the medium and easy to integrate into existing workflows or legacy systems via iFrame or API in less than a week.
Author
-

Sayem Shakir is a marketing and growth leader for AI, automation, and regulated technology platforms. He specialises in translating complex AI, data governance, and compliance driven products into clear, commercially relevant content for C suite and enterprise audiences. He has over 12 years of experience across marketing, sales, and strategy, with hands on leadership roles spanning fintech, legal tech, govtech, and enterprise AI. Sayem has led go to market strategy, demand generation, content, events, and partnerships, helping technology companies scale adoption in highly regulated industries. His work focuses on AI solutions, digital transformation, AI risk & governance, secure document intelligence, secure verification solutions, and automation in finance, healthcare, legal, education, and government. He regularly writes and advises on responsible AI adoption, risk, and compliance.